2 minute lesen
Corona-Virus ruft Hacker auf den Plan
Das Corona-Virus treibt die Bevölkerung, Gesundheitsbehörden, Politiker und Unternehmen in diesen Wochen um. Hackern liefert die aktuelle Situation...
News, Informationen und Tipps zum Thema IT Security. Schützen Sie Ihre Endgeräte mit der effektiven Sicherheitslösung von DriveLock.

2 minute lesen
Das Corona-Virus treibt die Bevölkerung, Gesundheitsbehörden, Politiker und Unternehmen in diesen Wochen um. Hackern liefert die aktuelle Situation...

2 minute lesen
Das große strategische Ziel von Cybersicherheit im digitalen Zeitalter ist die Bekämpfung und Eindämmung von Datenschutzverletzungen. Die Daten eines...
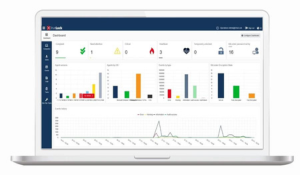
3 minute lesen
Der deutsche Spezialist für IT-Sicherheit unterstützt den Paradigmenwechsel in der IT Security mit neuen Funktionalitäten seiner voll integrierten...

2 minute lesen
TABLE OF CONTENT THE SHOCKING STATISTICS OF DATA BREACH ENCRYPTION MAKES DATA UNINTELLIGIBLE TO OUTSIDERS SOLUTION, THE DRIVELOCK WAY! THE SHOCKING...

4 minute lesen
Picture by Antonio Guillem | iStock by Mohamad Ashokaibi CFO: “I've lost my USB thumb drive. Lots of important spreadsheets were there! Do something...